We get it, running a business means juggling a hundred priorities at once, and password security often slips down the list. From our experience working with clients across a wide range of sectors (and dealing with their passwords), it’s clear that many still underestimate just how critical strong password practices are. But with so much of today’s business activity happening online, and sensitive data stored across multiple platforms, neglecting this area can leave your organisation wide open to threats.
It might feel tedious, even annoying, to manage different logins for every app and service. But the truth remains: weak passwords put your information at serious risk. Cybersecurity experts all agree on one thing: if you want to keep your accounts secure, you need robust passwords and, ideally, two-factor authentication (2FA) as a standard layer of protection.
To highlight just how vulnerable many users in the UK still are, our team produced this visual graphic using data gathered from a staggering 2.5 terabytes of leaked credentials collected from various data breaches in the U.K, reveals the most common passwords people are still using today.
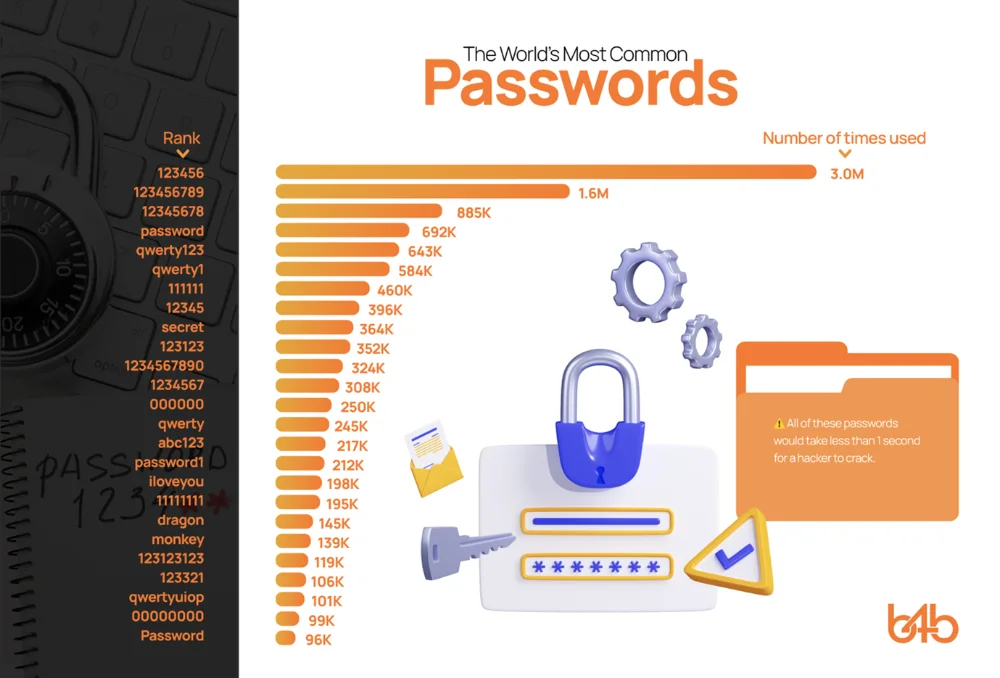
These aren’t guesses. These are real, exposed passwords that have appeared over and over again in breach databases.
The takeaway? If your passwords resemble anything on this list, it’s time for an urgent update.
As you can see, it may be surprising just how predictable some of these passwords are. Use it as a prompt to review your own password habits and encourage your colleagues and teams to do the same.
Our top tips for staying secure online:
- Use long, complex passwords, ideally with a mix of letters, numbers, and symbols.
- Avoid using the same password across multiple accounts.
- Enable two-factor authentication wherever possible.
- Consider using a reputable password manager or code generator for added convenience and security.
- Schedule regular updates for your credentials, especially for sensitive accounts like banking, email, or work system.
Keeping your data secure doesn’t have to be a headache, but it does require good habits and awareness. Don’t wait until after a breach to take action.











